
Redis is an open source in memory data structures store used as a database , cache and Message broker.
What is caching?
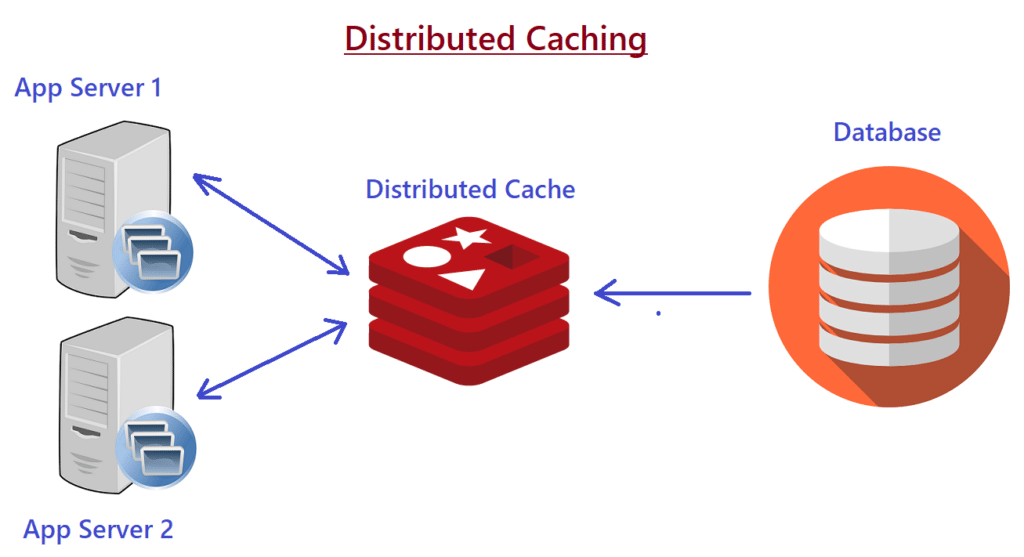
Caching is a process of storing data into a cache and cache is a temporary storage component area where the data is stored so that in future data can be served faster. In caching we don’t store our data on our secondary devices like hard disk, but we store our data into temporary storage from where we can access our data faster.
Redis is a no-sql database which follows the principle of key value store. So redis is a popular no-sql database. And when we try to access the data, then we specify the key to get the data.
Redis holds its database entirely in the memory, using that disk only for persistence. So when you run your redis, then all of your data is stored entirely in the memory.
And when you shut down your redis, then you have option to store your data on to the disk or not. If you opt in the option for your data to be stored on disk, then only your data is stored on disk, otherwise not, so redis uses your disk only for data persistence, not for accessing your data.
Redis hold your entire database in the memory, because if it will not do this, then redis will become slow and it will take some time. But Redis is not built for it. It’s built for speed.Redis supports data structures such as string, hashes, list set, sorted sets with range of queries, bitmap hyper log logs.So there are so much to cover for redis because there are many type of data structures available in redis.
Redis is written in ANSI C and it’s blazingly fast. Redis is being supported in most of the languages, by this point I mean to say that you can use your Redis with many different programming languages that are popular in the market like Python,Go, Java, C, C++ and many more.
Some Important Commands in Redis are listed below
- Set Key value
· Get Key
· DEL key1 key2 key3 (To delete a key).
· EXISTS key1 key2 (To check a key exist or not).
· TTL key (To check time to live).
· EXPIRE key 10(in seconds).
· PTTL mykey (to check time in millisecond).
· PEXPIRE mykey 1500 (Time in Milliseconds).
· PERSIST mykey (Remove EXPIRATION from the key)
· KEYS a?? (Returns all keys matching pattern)
· RANDOMKEY (Return a random key from the currently selected database)
· RENAME mykey myotherkey
· RENAMENX mykey myotherkey (Renames key to newkey if newkey does not yet exist)
· TOUCH key1 key2 (Alters the last access time of a key(s).
· UNLINK key1 key2 key3 (The actual removal will happen later asynchronously.)
· TYPE key1 (Return Type of Value)
· DUMP mykey (Serialize the value stored at the key in a Redis-specific format)
· RESTORE mykey 0 "\n\x17\x17\x00\x00\x00\x12\x00\x00\x00\x03\x00\”