Introduction
Delightitsolutions has spent many years assisting WordPress administrators in finding and fixing their hacked websites. We created this guide to help WordPress owners step by step in figuring out and cleaning up a hack. It may not cover everything, but if you follow it, it should help with many of the infections we often come across.
STEP 1
Find and identify the WordPress hack
1.1 Scan your WordPress site for malware and signs of infection
The initial step in eliminating malware from your WordPress site involves identifying the type of hack. This will aid in narrowing down the infection, making it easier to locate.
You can utilize tools that scan your site from a distance to detect harmful software and malware. For instance, delightitsolutions offers a free WordPress plugin available in the official WordPress repository. You can also use online tools to scan your site and pinpoint the location of harmful content and software
Scan WordPress for malware with Sitecheck:
SiteCheck is a completely free option to quickly scan your site for malware and other security issues.
To get started, simply enter the URL of a website, click Submit, and SiteCheck will begin a remote scan of the domain’s public pages.
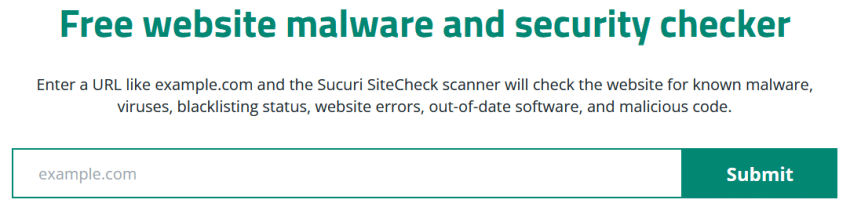
A scan from a distance will examine your WordPress site to find possible security problems. Some problems may not appear in a web browser. Instead, they appear on the server, like hidden entrances, misleading links, and scripts on the server. The most thorough way to scan involves using both remote and server-side scanners For more detailed results, you can request delightitsolutions’ team to conduct a run a server-side scan of your website.
If the scan from a distance can’t find any harmful software, proceed with other tests in this section. You can also manually check the iFrames / Links / Scripts in the Malware Scan for elements that seem strange or suspicious.
If you have many WordPress sites on the same server, we suggest scanning all of them (you can use SiteCheck for this). Contamination between different sites on the same server is a major reason for getting infected again. We strongly recommend that every website owner isolate their sites in their own hosting environments.
To examine the page requests on your website, follow these steps:
- Head to the WebPage Test website.
- Input your website and initiate the test by clicking on Start Test.
- Navigate to the waterfall result.
- Assess the request details.
- Take note of any requests that appear suspicious or unrecognized.
This external tool offers insights into the content loading on your WordPress site. By reviewing all the page requests made during your site’s loading process, you can effectively pinpoint any potentially harmful or undesired domains loading on your site.
To scrutinize external domains loading on your site, you have several methods to choose from:
- SiteCheck: Use SiteCheck to search for suspicious domain names and check if they are being blocklisted.
- Google: Conduct a Google search for a domain name using “site:example.com” within Google, then review the results. Exercise caution and avoid clicking on results from domains you don’t trust. Simply review them to determine if they might be related to your site’s code (e.g., domains used by plugin authors, theme authors, etc.).
- URLScan.io: Search for URL results using URLScan.io to gather comprehensive information about a site. This includes details on where the site is hosted, the actions of the requests, and an overall understanding of the site’s behavior without direct access.
- VirusTotal: Utilize VirusTotal to search for domain results, serving as a free blocklist vendor checker. The results will include:
- Detection: Check the website’s blocklist status from 70+ vendors.
- Details: View the site’s history and HTTP response.
- Links: Review any outgoing links.
- Community: Read comments from the public regarding the safety of a site
Pro Tip
If you do not recognize a domain name loading on your site and would like to research it, refrain from visiting the domain directly. Instead, perform the tips listed below to mitigate risk.
Looking for assistance in removing malware from your WordPress site?
Our expert incident response team can swiftly clean your WordPress site. We’re available round-the-clock, every day of the year!
1.2 Check core WordPress file integrity
WordPress websites have many important files that should not be changed. These files are a crucial part of WordPress and are found in the main folder, wp-includes, and wp-admin directories. It’s essential to check if any of these core files have been modified in a harmful way.
Here are different ways to manually check if these core files have been changed on a website built with WordPress.
How to compare two text files with Diffchecker:
- Visit the D Diffchecker website.
- Paste the original text of a clean core file into the ‘Original Text’ box.
- Paste the modified core file text into the ‘Changed Text’ box.
- Click ‘Find Difference’ at the bottom.
- Review the differences in the text.
- Note down any suspicious code differences.
If you find modifications in your core files, it might be infected. Continue checking more core files as others may also be infected. If nothing has been modified, your core files are clean.
How to compare two files via SSH:
- Log into your server using SSH.
- Create a test directory and paste the clean core file text into a test .txt file inside it.
- Paste the modified core file text into another test .txt file in the same directory.
- Run the command
$ diff test1.txt test2.txt
If there are modifications, this file may be hacked.
Sometimes, minor changes to these files may not indicate a hack. However, obfuscated code in a core file is a sign that something malicious may be present. Obfuscated code is written in a way that needs decoding to understand and is often used by attackers to hide their malicious code.
If you find obfuscated code in your files, here are some tools to help decode the content:
- Base64 Decode: Decodes base64 encoded strings.
- UnPHP:Decodes obfuscated malicious PHP code.
- harCode Translator: Decodes CharCode.
- OnlinePHP.io: Decodes and tests PHP code.
- UnPacker: Unpacks messy code.
1.3 Check for recently modified files:
New or recently modified files might be part of the hack. There are different ways to check recently modified files, such as using cPanel or SSH.
How to check recently modified files via SSH with the ls command:
- Log into your server using SSH and navigate to your site’s home directory.
- Run the following command:
$ ls -1tlah | head -10
- Review the most recently modified files, starting at the top.
How to check recently modified files via SSH with the find command:
- Log into your server using SSH and navigate to your site’s home directory.
- Run the following command:
$ find . -type f -mtime -90Results will show files modified within the last 90 days. Review these files. Unfamiliar modifications within the last 90 days may be suspicious.
How to check recently modified files from cPanel:
- Log into cPanel and go to File Manager.
- Navigate to your site’s home directory and click ‘Last Modified’.
- View files with recently modified dates, starting at the top.
How to check recently modified files with Filezilla:
- Open FileZilla and connect to your website through FTP, FTPs, or sFTP.
- Go to View in the top menu and select ‘Filename filters…’.
- Select ‘New’ to create a new filter.
- Name your filter, such as ‘Date Filter‘.
- Add the filter criteria. For ‘Filter conditions:’, select ‘Filter out items matching none of the following‘.
- Select ‘Date’ and enter the date you are looking for in the format “YYYY-MM-DD”.
- Check the box next to your filter, select ‘Apply’, and then select ‘OK’ to close the window.
This will filter out files not modified within the specified date range of 15 days , allowing you to look through each directory quickly to find recent modifications while searching for malware.
You will need to follow these steps to change the filter dates or start a new search.”
“1.4 Check Google diagnostic pages for warnings
If your WordPress website is hacked and blocklisted by Googleor other website security authorities, you can use their diagnostic tools to check how secure your website is.
How to check your Google Transparency Report:
1. Go to the Safe Browsing Site Status website.
2. Enter your site’s URL and search.
3. On this page, you can check:
– Site Safety Details: Information about harmful redirects, spam, and downloads.
– Testing Details: The most recent Google scan that found malware.
If you’ve added your site to any free webmaster tools, you can check their security ratings and reports for your website. If you haven’t signed up for these free monitoring tools, we strongly recommend that you do so:
–
If your website is listed on any major blocklisting vendors, you can use VirusTotal to analyze the issue.
How to check your website on VirusTotal
1. Visit the VirusTotal website.
2. Click the URL tab, enter your site’s URL, and search.
3. On this page, you can check:
– Detection: : Check if your website is blocked by 70+ vendors.
– Details: View the history and HTTP response from your site.
– Links: Review any outgoing links.
– Community: Review comments from the public about the safety of your site.”
STEP 2
Remove malware from your WordPress site and database
Now that you can find where the bad stuff is, you can clean it out and have a safe, working WordPress site.
The steps below need access to the WordPress files and database. You’ll need access through sFTP, FTP, or SSH to see your file structure, and the database credentials to get into your database. Make sure to create a complete backup of your website before you start these steps!
If you’re not comfortable with changing database tables or editing PHP, please ask for help from a professional Incident Response Team member who can completely remove website malware For You.
Now that you can find where the bad stuff is, you can clean it out and have a safe, working WordPress site.
The steps below need access to the WordPress files and database. You’ll need access through sFTP, FTP, or SSH to see your file structure, and the database credentials to get into your database. Make sure to create a complete backup of your website before you start these steps!
If you’re not comfortable with changing database tables or editing PHP, please ask for help from a professional Incident Response Team member who can completely remove website malware For You.
Pro Tip
The best way to remove malware and identify hacked files in WordPress is by comparing the current state of the site with an old and known to be clean backup. If a backup is available, you can use that to compare the two versions and identify what has been modified. A restore may be the fastest option to get your site functional again.
2.1 Clean Compromised WordPress Files
WordPress comprises numerous files and folders that collaborate to establish a functional website. Most of these files are core files, providing consistent structure across installations of the same version.
If malware has infiltrated your core files, you can manually remove it by obtaining a fresh installation from the official WordPress site and replacing each compromised file with a clean copy. However, exercise caution to not overwrite your wp-config.php file or wp-content folder, and ensure you possess a functional backup before proceeding!
Steps to Clean Compromised WordPress Core Files:
- Record the version of your WordPress site by inspecting the file wp-includes/version.php.
- Visit the official WordPress site and download the version corresponding to your wp-includes/version.php file.
- Extract the WordPress installation on your computer.
- Access your file structure either via sFTP/FTP or your hosting account.
- Substitute each infected core file with a clean copy.
Steps to Manually Clean Hacked WordPress Plugin and Theme Files:
- Obtain a clean plugin/theme copy from a functional backup or from the official WordPress site.
- Extract the plugin/theme copy on your computer.
- Access your file structure either via sFTP/FTP or your hosting account.
- Replace the relevant plugin/theme folder within ./wp-content/plugins or ./wp-content/themes with the clean copy.
- Open any custom or premium files (not in the official repository) with a text editor.
- Eliminate any suspicious code from the custom files.
- Test to confirm that the site remains operational after the modifications.
Important Note: Ensure that if plugins or themes have been customized in any way, you restore them from a clean backup to avoid losing any modifications you have made.
How to Clean a Hacked WordPress Plugin via the Dashboard:
- Log into your WordPress dashboard and go to the Installed Plugins section under Plugins.
- Deactivate and delete the relevant plugins.
- Install and activate each plugin from the dashboard or upload a clean copy from a functional backup.
2.1 Clean Compromised WordPress Files
WordPress comprises numerous files and folders that collaborate to establish a functional website. Most of these files are core files, providing consistent structure across installations of the same version.
If malware has infiltrated your core files, you can manually remove it by obtaining a fresh installation from the official WordPress site and replacing each compromised file with a clean copy. However, exercise caution to not overwrite your wp-config.php file or wp-content folder, and ensure you possess a functional backup before proceeding!
Steps to Clean Compromised WordPress Core Files:
- Record the version of your WordPress site by inspecting the file wp-includes/version.php.
- Visit the official WordPress site and download the version corresponding to your wp-includes/version.php file.
- Extract the WordPress installation on your computer.
- Access your file structure either via sFTP/FTP or your hosting account.
- Substitute each infected core file with a clean copy.
Steps to Manually Clean Hacked WordPress Plugin and Theme Files:
- Obtain a clean plugin/theme copy from a functional backup or from the official WordPress site.
- Extract the plugin/theme copy on your computer.
- Access your file structure either via sFTP/FTP or your hosting account.
- Replace the relevant plugin/theme folder within ./wp-content/plugins or ./wp-content/themes with the clean copy.
- Open any custom or premium files (not in the official repository) with a text editor.
- Eliminate any suspicious code from the custom files.
- Test to confirm that the site remains operational after the modifications.
Important Note: Ensure that if plugins or themes have been customized in any way, you restore them from a clean backup to avoid losing any modifications you have made.
How to Clean a Hacked WordPress Plugin via the Dashboard:
- Log into your WordPress dashboard and go to the Installed Plugins section under Plugins.
- Deactivate and delete the relevant plugins.
- Install and activate each plugin from the dashboard or upload a clean copy from a functional backup.
Caution
Do not replace any content within the wp-content directory or replace the wp-config.php file.
2.2 Clean Hacked Database Tables
To Get Rid of from malware infection from your WordPress database, you’ll need to use your database admin panel or tools like PHPMyAdmin or Adminer.
Manually Removing Malware from Your WordPress Database
If your WordPress database is infected with malware, follow these steps to manually remove the infection:
- Access your database admin panel and log in.
- Prior to making any changes, create a backup of the database.
- Look for any suspicious content, such as spammy keywords or malicious links.
- Identify the specific row containing the suspicious content.
- Manually remove the detected suspicious content from the respective row.
- Test the site’s functionality to ensure it remains operational after the removal.
- If you’ve uploaded any database access tools, be sure to remove them.
For those new to handling malware issues, leverage the payload details offered by the malware scanner. For more experienced users, a manual review for typical malicious PHP functions like eval, base64_decode, gzinflate, preg_replace, str_replace, and others is recommended.
Sometimes, you might observe an abrupt surge in spam posts or unusual content on your website, indicating a potential hack. This can happen if an administrator’s password has been compromised. Stay vigilant and take appropriate action to secure your site.
How to move WordPress posts to the trash after a specific date:
- Log in to your database admin panel.
- Prior to making any changes, create a backup of the database.
- Go to SQL Command at the top left.
- Take note of your WordPress database prefix, typically ‘wp_’.
- Identify the date when the spam posts commenced.
- Execute the following SQL Command:
Warning
Keep in mind that legitimate plugins also rely on these functions. Ensure you test any modifications or seek assistance to avoid unintentional site disruptions. When working with database records, replacing data, especially within the wp_options table, may not always be straightforward.
How to move WordPress posts to the trash after a specific date:
- Log in to your database admin panel.
- Prior to making any changes, create a backup of the database.
- Go to SQL Command at the top left.
- Take note of your WordPress database prefix, typically ‘wp_’.
- Identify the date when the spam posts commenced.
- Execute the following SQL Command:
UPDATE `wp_posts` SET `post_status` = ‘trash’ WHERE `post_status` = ‘publish’ AND `post_type` = ‘post’ AND `post_date` > ‘2023/03/08’;
Important:
Ensure you replace the date in the provided SQL command with the relevant date when you first observed the spam posts. In the given example, it will delete posts dated March 9th, 2023 and newer.
Also, verify that the date format matches the display in your dashboard, which can be checked at the top right of your posts section.
2.3 Ensuring the Security of WordPress User Accounts:
Attackers frequently create malicious admin or FTP users to regain access to your site later. Therefore, it’s crucial to thoroughly review user account access from all possible entry points into your site. If a WordPress site gets infected and is cleaned, but the malicious admin/FTP users remain, the site is at risk of swift re-infection.
Remove any users you don’t recognize to deny hackers access, including:
- FTP Users
- SSH Users
- WordPress Admin Users
- Additional Database Users
How to manually remove suspicious users from WordPress:
- Back up your site and database before proceeding.
- Log into WordPress as an admin and go to Users.
- Identify suspicious new user accounts.
- Hover over the suspicious user and click Delete.
- If a user has associated content, you’ll be prompted to keep or remove any linked content. It’s advisable to keep the content and manage it later to prevent unintentional data loss.
If you suspect any compromise of user accounts, reset their passwords. One method is using the Sucuri WordPress plugin.
We recommend designating only one admin user and assigning other user roles with the least privileges necessary (e.g., contributor, author, editor).
Note:
Some types of malware infections may create unauthorized email accounts if the option is available on your hosting platform. (For instance, the Anonymous Fox infection.) Log in to your hosting account and check the Email Accounts section, if available. Remove any users that you do not recognize
2.3 Ensuring the Security of WordPress User Accounts:
Attackers frequently create malicious admin or FTP users to regain access to your site later. Therefore, it’s crucial to thoroughly review user account access from all possible entry points into your site. If a WordPress site gets infected and is cleaned, but the malicious admin/FTP users remain, the site is at risk of swift re-infection.
Remove any users you don’t recognize to deny hackers access, including:
- FTP Users
- SSH Users
- WordPress Admin Users
- Additional Database Users
How to manually remove suspicious users from WordPress:
- Back up your site and database before proceeding.
- Log into WordPress as an admin and go to Users.
- Identify suspicious new user accounts.
- Hover over the suspicious user and click Delete.
- If a user has associated content, you’ll be prompted to keep or remove any linked content. It’s advisable to keep the content and manage it later to prevent unintentional data loss.
If you suspect any compromise of user accounts, reset their passwords. One method is using the Sucuri WordPress plugin.
We recommend designating only one admin user and assigning other user roles with the least privileges necessary (e.g., contributor, author, editor).
How to eliminate malware warnings for your site:
Contact your hosting company and request the removal of the suspension if your website has been suspended by your hosting provider. You may need to provide information about how you resolved the malware issue.
Complete a review request form for each blocklisting authority. We’ve compiled helpful guides on how to remove Google warnings or address McAfee SiteAdvisor warnings. Additionally, ensure to check other well-known search authorities like Bing, Norton, or Yandex.
Need assistance?
The delightitsolutions Website Security Platform can assist in submitting blocklist and malware warning removal requests on your behalf. This service helps ensure your site is fully prepared for review.
STEP 3
Secure your WordPress site against future hacks.
In this final step, you will learn how to fix the issues that caused your WordPress to be hacked in the first place. You will also perform essential steps to enhance the security of your WordPress site.
3.1 Update Outdated Software:
Outdated software is a major vulnerability that can lead to infections. This encompasses the WordPress version, plugins, themes, and any other software components installed on the site. Plugin and theme authors frequently release critical vulnerability patches, making it vital to keep up with the latest updates.
Ensure all software on your server (e.g., Apache, cPanel, PHP) is updated to eliminate any missing security patches.
This includes:
- Updating outdated plugins
- Updating outdated themes
- Updating Apache version
- Updating PHP version
- Updating WHM/cPanel version
- Updating WordPress version
It’s recommended to reinstall all plugins and extensions after a hack to ensure their functionality and confirm they are free of any remaining malware.
Pro Tip
You can deactivate a plugin or theme first and test the functionality of your website before deleting unused software.
3.2 Enhancing Security by Updating User Passwords
It’s crucial to change passwords for all entry points to your WordPress site, including WordPress user accounts, FTP/SFTP, SSH, cPanel, and your database.
Follow these key steps to bolster password security:
Minimize Admin Accounts: Reduce the number of admin accounts to the absolute minimum. Adhere to the principle of least privilege, granting access based on necessity and duration.
Use Strong Passwords: Ensure all accounts have strong passwords that emphasize complexity, length, and uniqueness. Tools like Passwords Generator can assist in creating secure passwords. Utilize a password manager to keep track of these.
Generate New Secret Keys: After resetting passwords, force all users to log off, particularly by resetting WordPress secret keys to invalidate existing sessions. Here’s how you can generate new secret keys in the wp-config.php file:
- Open the WordPress wp-config.php file.
- Assign a value of 60+ unique characters for each key and salt.
- Utilize a secret key generator.
- Save the wp-config.php file.
3.3 Strengthening Your WordPress Site Security
Harden your WordPress site to minimize vulnerabilities and fortify your defenses against potential attacks. Here are key measures to enhance security:
Limit Entry Points: Reduce access points to your website, allowing public access only to intended areas. Employ server configuration rules or a web application firewall to deny access to unauthorized sections.
Regular Updates: Keep both your website and server up to date. Outdated software is a primary cause of infections and subsequent reinfections. Regular updates bolster your site’s security.
Password Security and Multi-factor Authentication: Enhance security by using lengthy, secure, and random passwords for FTP and administrative access. Additionally, enforce multi-factor authentication to restrict access to administrative panels.
Isolate Your Website: Prevent cross-contamination, a significant source of infections and reinfections, by isolating each website in its hosting plan. Follow these steps:
- Backup and remove unused websites.
- Migrate each website to its dedicated hosting plan.
- Assign a dedicated user for each website, limiting access to files associated with the respective site.
Explore more WordPress hardening methods in the WordPress Codex based on your specific requirements. Additionally, refer to the Website Firewall section for insights on virtual patching and hardening.
3.4 Establish Regular Backup Procedures for Your WordPress Site
Regular backups serve as a safety net, crucial for maintaining a robust security posture for your WordPress site. Follow these guidelines to effectively manage backups:
Location: Store your backups in an off-site location. Avoid keeping backups or older versions on your server, as they can serve as potential entry points for attackers if not managed securely. Ensure your working backups are stored in various locations for added security.
Automation: Opt for an automated backup solution that aligns with your website’s update frequency. For instance, if your website is frequently updated, set up backups to run at appropriate intervals.
Redundancy: Implement a redundancy strategy to guarantee emergency backups of critical data in case of a catastrophic event. Maintain functional backups and create additional copies for added security.
Testing: Regularly test your backups to confirm their integrity and functionality in case a restoration is necessary. Rely on backups only when they’ve been tested and confirmed to be clean from any malware.
Inclusive File Types: Ensure your backup solution includes all file types, even large ones like videos and archives. Confirm that every crucial element is encompassed in your backup for comprehensive protection.
Perform a malware scan on your computer. Ensure that all WordPress users conduct a thorough malware scan using a reliable antivirus program on their operating systems.
WordPress security is at risk if a user with a compromised computer gains access to the dashboard. Certain infections are crafted to transfer from a computer to text editors or FTP clients.
Recommended Paid Antivirus Programs:
- Bitdefender
- Kaspersky
- Sophos
- F-Secure
Recommended Free Antivirus Programs:
- Malwarebytes
- Avast
- Microsoft Security
- Avira
It’s crucial to maintain a clean computer; otherwise, your website may easily fall prey to reinfection.
Did you know
Delightitsolutions offers its customers an affordable system for secure website backups.
3.5 Scan your computer for malware
Perform a malware scan on your computer. Ensure that all WordPress users conduct a thorough malware scan using a reliable antivirus program on their operating systems.
WordPress security is at risk if a user with a compromised computer gains access to the dashboard. Certain infections are crafted to transfer from a computer to text editors or FTP clients.
Recommended Paid Antivirus Programs:
- Bitdefender
- Kaspersky
- Sophos
- F-Secure
Recommended Free Antivirus Programs:
It’s crucial to maintain a clean computer; otherwise, your website may easily fall prey to reinfection.
Helpful Tip:
It’s advisable to have only a single antivirus actively safeguarding your system to prevent conflicts
Section 3.6: Utilize a Website Firewall for Malware Prevention
The frequency of vulnerabilities being exploited by malicious attackers is increasing daily, posing a constant challenge for administrators. Keeping up with these threats can be difficult. Website Firewalls were developed to create a defensive perimeter around your WordPress site, helping filter out malicious requests to your server.
The benefits of using a website firewall are as follows:
Prevent Future Hacks: By detecting and stopping known hacking methods and behaviors, a website firewall can effectively protect your site against potential future attacks.
Virtual Security Update: Hackers exploit vulnerabilities in plugins and themes rapidly, including emerging unknown ones known as zero-day exploits. A reliable website firewall will patch these vulnerabilities in your website software, even if you haven’t applied the latest security updates.
Block Brute Force Attacks: A website firewall should prevent unauthorized access to your wp-admin or wp-login page, ensuring that brute force automation cannot guess your password. Various features are utilized to deter brute force attacks, such as time delays, limitations on login attempts, IP address blocklisting, and more.
Mitigate DDoS Attacks: Distributed Denial of Service (DDoS) attacks attempt to overwhelm your server or application resources. By detecting and blocking all types of DDoS attacks, a website firewall ensures your site remains available even during high-volume fake visit attacks.
Performance Optimization: Most Web Application Firewalls (WAFs) offer caching to enhance global page speed. This not only enhances visitor satisfaction but has been proven to reduce bounce rates, improve website engagement, increase conversions, and boost search engine rankings.